Introduction
Breach Notifications play a critical role in today’s digital world where data is constantly collected, stored, and shared. Businesses of all sizes handle personal and sensitive information every day, including names, emails, passwords, and payment details. When this information is exposed due to a security incident, the impact can be serious. Customers may lose trust, legal penalties may apply, and long-term brand damage can follow. That is why understanding Breach Notifications Hacking Alerts is no longer optional for modern organizations.
In simple terms, Breach Notifications are official messages sent to affected individuals and authorities after a data breach occurs. These notifications explain what happened, what information was involved, and what steps are being taken to fix the issue. For beginners, this topic may sound technical or legal, but the core idea is very practical. It is about honesty, responsibility, and protection of people’s data.
For intermediate readers, Breach Notifications also involve compliance, timing, documentation, and communication strategy. Different regions have different rules, but the main goal remains the same. Organizations must act quickly and clearly. When done correctly, Breach Notifications can reduce confusion, limit damage, and even help rebuild trust.
This guide explains Breach Notifications in simple English. You will learn what they are, why they matter, how to handle them step by step, and what mistakes to avoid. By the end, you will have a clear and practical understanding that you can apply confidently.
What is Breach Notifications?

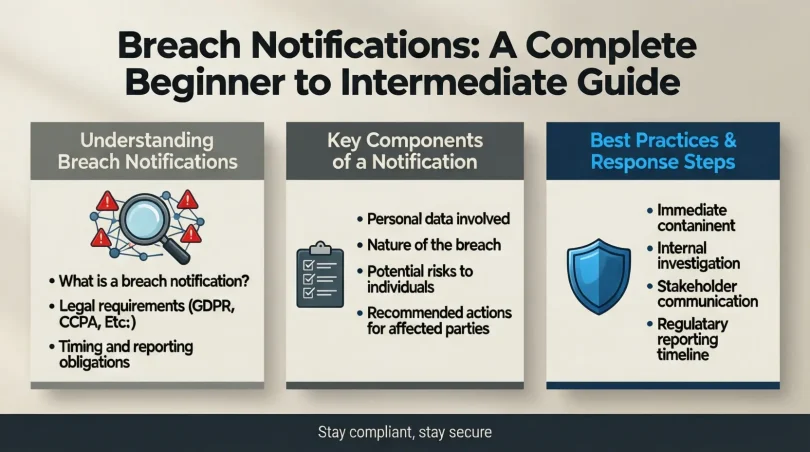
Breach Notifications refer to the formal process of informing individuals, customers, partners, and authorities about a data breach. A data breach happens when unauthorized access, disclosure, or loss of sensitive information occurs. This information may include personal data, financial records, login credentials, or confidential business details.
The purpose of Breach Notifications is to ensure transparency and allow affected people to take protective action. For example, users may change passwords, monitor accounts, or freeze credit reports after receiving a notification. From a business perspective, these notifications demonstrate accountability and compliance with data protection laws.
Breach Notifications usually include several key elements. These elements explain what happened, when it happened, what data was affected, and what steps are being taken to prevent future incidents. They also provide guidance on what affected individuals should do next.
Many countries have laws that make Breach Notifications mandatory. These laws often specify timelines, communication methods, and penalties for noncompliance. Even when not legally required, many organizations still choose to send Breach Notifications as a best practice.
In short, Breach Notifications are not just legal documents. They are communication tools that protect people, reduce confusion, and show responsible behavior after a security incident.
Why is Breach Notifications Important?
Breach Notifications are important because they protect both individuals and organizations. When people know their data may be at risk, they can take immediate steps to reduce harm. This may include changing passwords, watching bank statements, or being alert to phishing attempts.
From a legal standpoint, Breach Notifications help organizations comply with data protection regulations. Failure to notify on time can result in fines, lawsuits, and regulatory investigations. Even worse, hiding a breach can cause reputational damage that lasts for years.
Trust is another major reason Breach Notifications matter. Customers expect honesty. When a company communicates openly during a crisis, it shows respect for users and their data. Clear communication can reduce panic and prevent misinformation.
Breach Notifications also help internal teams learn from mistakes. By documenting what went wrong and sharing corrective actions, organizations can improve their security posture. This process reduces the risk of similar incidents in the future.
Finally, Breach Notifications support ethical business practices. They reflect a commitment to transparency and responsibility in a digital environment where data misuse is a growing concern.
Detailed Step-by-Step Guide
Step 1: Identify the Breach
The first step is detecting and confirming the breach. This involves monitoring systems, reviewing logs, and verifying unusual activity. False alarms should be ruled out before moving forward.
Step 2: Contain the Incident
Once confirmed, the breach must be contained immediately. This may include disabling affected systems, changing access credentials, or blocking unauthorized users. Quick action limits further damage.
Step 3: Assess the Impact
Next, determine what data was affected and how many individuals are involved. This assessment helps decide the scope of Breach Notifications and the urgency of communication.
Step 4: Review Legal Requirements
Different regions have different notification laws. Organizations must check applicable regulations to understand timelines and reporting obligations. Legal teams often assist at this stage.
Step 5: Prepare the Notification Message
The notification should be clear, honest, and easy to understand. Avoid technical jargon. Explain what happened, what data was involved, and what steps are being taken.
Step 6: Notify Authorities if Required
Some laws require notifying data protection authorities before or alongside affected individuals. These reports usually include technical details and mitigation plans.
Step 7: Inform Affected Individuals
Send Breach Notifications through appropriate channels such as email or letter. Make sure the message reaches the right audience without causing unnecessary alarm.
Step 8: Offer Support and Guidance
Provide practical advice such as password changes or account monitoring. In some cases, offering credit monitoring services may be appropriate.
Step 9: Document Everything
Keep records of the breach, decisions made, and notifications sent. Documentation is important for audits, investigations, and future improvement.
Step 10: Improve Security Measures
After notifications are sent, review security controls and update policies. Lessons learned should lead to stronger protection going forward.
Benefits of Breach Notifications
- Builds trust through transparency and honesty
- Helps individuals protect themselves quickly
- Supports compliance with data protection laws
- Reduces legal and financial risks
- Improves internal security awareness
- Demonstrates ethical business behavior
- Limits misinformation and rumors
- Encourages continuous security improvement
Disadvantages / Risks
- May cause short-term reputational damage
- Can lead to legal scrutiny or investigations
- Requires time, resources, and coordination
- Poorly written notifications may create panic
- Over-notification can lead to message fatigue
- Incomplete information may reduce credibility
Common Mistakes to Avoid
One common mistake is delaying Breach Notifications. Waiting too long can violate laws and damage trust. Speed matters, even if all details are not yet known.
Another mistake is using complex or technical language. Notifications should be written for general audiences, not security experts. Confusing messages reduce effectiveness.
Some organizations also downplay the incident. Minimizing the impact may seem tempting, but it often backfires when more details emerge later.
Failing to provide clear next steps is another issue. People want to know what actions they should take to stay safe.
Finally, forgetting internal communication can cause problems. Employees should be informed so they can respond consistently to questions.
FAQs
What triggers Breach Notifications?
Breach Notifications are triggered when sensitive or personal data is accessed, disclosed, or lost without authorization. This includes hacking, accidental sharing, or system errors.
Are Breach Notifications legally required?
In many regions, yes. Data protection laws often require notifications within specific timeframes. Requirements vary by location and type of data.
How fast should notifications be sent?
Timelines depend on regulations, but many laws require notification within days of discovering the breach. Prompt action is always recommended.
Who should receive Breach Notifications?
Affected individuals, relevant authorities, and sometimes business partners should be notified. The audience depends on the breach scope.
What information should be included?
Notifications should explain what happened, what data was affected, potential risks, and recommended actions. Contact information for support should also be included.
Can Breach Notifications be sent by email?
Yes, email is common, but it must be secure and reliable. In some cases, letters or public notices may be required.
Expert Tips & Bonus Points
Always prepare a breach response plan before an incident happens. Planning reduces stress and mistakes during real events.
Use templates for Breach Notifications, but customize them for each incident. Generic messages feel insincere and may miss key details.
Train staff regularly on data protection and incident reporting. Early detection often starts with employee awareness.
Test your notification process through drills. Practice reveals gaps and improves response time.
Finally, treat Breach Notifications as part of a larger trust strategy. Honest communication today can protect your reputation tomorrow.
Conclusion
Breach Notifications are a vital part of responsible data management in the digital age. As organizations collect and process more information, the risk of data breaches continues to grow. Knowing how to respond correctly makes a significant difference. Breach Notifications are not just about legal compliance. They are about protecting people, maintaining trust, and showing accountability when things go wrong.
For beginners, understanding the basics of Breach Notifications removes fear and confusion. The process is logical and focused on communication. For intermediate readers, refining notification strategies improves efficiency and credibility. Clear steps, timely action, and honest messaging form the foundation of effective response.
While Breach Notifications may feel uncomfortable, avoiding them is far more damaging. Transparency helps control the narrative and reduces long-term harm. Each incident also offers a chance to learn and strengthen security practices.
In the end, Breach Notifications reflect how an organization values data and people. When handled with care, they can turn a difficult situation into an opportunity to demonstrate integrity, responsibility, and commitment to improvement.